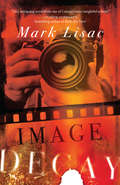- Table View
- List View
Ilse Koch on Trial: Making the “Bitch of Buchenwald”
by Tomaz JardimAn authoritative reassessment of one of the Third Reich’s most notorious war criminals, whose alleged sexual barbarism made her a convenient scapegoat and obscured the true nature of Nazi terror.On September 1, 1967, one of the Third Reich’s most infamous figures hanged herself in her cell after nearly twenty-four years in prison. Known as the “Bitch of Buchenwald,” Ilse Koch was singularly notorious, having been accused of owning lampshades fabricated from skins of murdered camp inmates and engaging in “bestial” sexual behavior. These allegations fueled a public fascination that turned Koch into a household name and the foremost symbol of Nazi savagery. Her subsequent prosecution resulted in a scandal that prompted US Senate hearings and even the intervention of President Truman.Yet the most sensational atrocities attributed to Koch were apocryphal or unproven. In this authoritative reappraisal, Tomaz Jardim shows that, while Koch was guilty of heinous crimes, she also became a scapegoat for postwar Germans eager to distance themselves from the Nazi past. The popular condemnation of Koch—and the particularly perverse crimes attributed to her by prosecutors, the media, and the public at large—diverted attention from the far more consequential but less sensational complicity of millions of ordinary Germans in the Third Reich’s crimes.Ilse Koch on Trial reveals how gendered perceptions of violence and culpability drove Koch’s zealous prosecution at a time when male Nazi perpetrators responsible for greater crimes often escaped punishment or received lighter sentences. Both in the international press and during her three criminal trials, Koch was condemned for her violation of accepted gender norms and “good womanly behavior.” Koch’s “sexual barbarism,” though treated as an emblem of the Third Reich’s depravity, ultimately obscured the bureaucratized terror of the Nazi state and hampered understanding of the Holocaust.
Image Analysis and Recognition: 15th International Conference, ICIAR 2018, Póvoa de Varzim, Portugal, June 27–29, 2018, Proceedings (Lecture Notes in Computer Science #10882)
by Aurélio Campilho Fakhri Karray Bart ter Haar RomenyThis book constitutes the thoroughly refereed proceedings of the 15th International Conference on Image Analysis and Recognition, ICIAR 2018, held in Póvoa de Varzim, Portugal, in June 2018.The 91 full papers presented together with 15 short papers were carefully reviewed and selected from 179 submissions. The papers are organized in the following topical sections: Enhancement, Restoration and Reconstruction, Image Segmentation, Detection, Classication and Recognition, Indexing and Retrieval, Computer Vision, Activity Recognition, Traffic and Surveillance, Applications, Biomedical Image Analysis, Diagnosis and Screening of Ophthalmic Diseases, and Challenge on Breast Cancer Histology Images.
Image Decay
by Mark LisacMark Lisac’s Image Decay returns to the pugnacious world of backroom politics laid out in his award-nominated Where the Bodies Lie. Set again in that “unnamed capital city east of the Rockies,” where the Brutalist architecture of the downtown core reflects the body politic laid bare.When a cantankerous ex-government photographer seeks ownership of his prints, the powers-that-be are determined to prevent the release of certain sensitive photos. Set in the 1990s, this political thriller delves into questions of identity and memory, established power and its fears and secrets, old stock versus newcomers, belonging and alienation.Image Decay investigates the intricacies of political manipulation, personal anxieties, and how history must be seen to be confronted.
Image Reconstruction in Radiology
by J. A. ParkerThis one-of-a-kind resource provides a very readable description of the methods used for image reconstruction in magnetic resonance imaging, X-ray computed tomography, and single photon emission computed tomography. The goal of this fascinating work is to provide radiologists with a practical introduction to mathematical methods so that they may better understand the potentials and limitations of the images used to make diagnoses. Presented in four parts, this state-of-the-art text covers (1) an introduction to the models used in reconstruction, (2) an explanation of the Fourier transform, (3) a brief description of filtering, and (4) the application of these methods to reconstruction. In order to provide a better understanding of the reconstruction process, this comprehensive volume draws analogies between several different reconstruction methods. This informative reference is an absolute must for all radiology residents, as well as graduate students and professionals in the fields of physics, nuclear medicine, and computer-assisted tomography.
Images in Law
by William PencakWhat does 'the law' look like? While numerous attempts have been made to examine law and legal action in terms of its language, little has yet been written that considers how visual images of the law influence its interpretation and execution in ways not discernible from written texts. This groundbreaking collection focuses on images in law, featuring contributions that show and discuss the perception of the legal universe on a theoretical basis or when dealing with visual semiotics (dress, ceremony, technology, etc.). It also examines 'language in action', analyzing jury instructions, police directives, and how imagery is used in conjunction with contentious social and political issues within a country, such as the image of family in Ireland or the image of racism in France.
Images of Anarchy
by Ioannis D. EvrigenisHobbes's concept of the natural condition of mankind became an inescapable point of reference for subsequent political thought, shaping the theories of emulators and critics alike, and has had a profound impact on our understanding of human nature, anarchy, and international relations. Yet, despite Hobbes's insistence on precision, the state of nature is an elusive concept. Has it ever existed and, if so, for whom? Hobbes offered several answers to these questions, which taken together reveal a consistent strategy aimed at providing his readers with a possible, probable, and memorable account of the consequences of disobedience. This book examines the development of this powerful image throughout Hobbes's works, and traces its origins in his sources of inspiration. The resulting trajectory of the state of nature illuminates the ways in which Hobbes employed a rhetoric of science and a science of rhetoric in his relentless pursuit of peace.
Images of Europe: The Union between Federation and Separation (Law and Visual Jurisprudence #4)
by Francesco Mangiapane Tiziana MiglioreThis book deals with the fundamental semantics of images of Europe, which consist of valences, mirror beliefs and affectivities. This is why it relaunches the importance of the European discourse in its symbolic dimension. As such, it explores the many images of Europe, or rather the many images through which European discourse is actually constituted in daily life, in search of their enunciative responsibility in today’s world for determining the current “State of the Union”. The identity of the European continent is based on a millenary tension between universalism and particularism: images of Europe have in fact been alternately inspired, over the centuries, by a model of homogeneity – Roman and Carolingian imperial disposition – on the one hand, and by a model of fragmentation – a Europe of city-states, municipalities, regions and small fatherlands – on the other. In the European Union, a political and economic organism, this issue has recently been amplified to the point that it has reentered public debate, and political parties that are only recognizable for being Europeanists or anti-Europeanists are now ubiquitous. In this regard, one major bone of contention is how to portray the quintessential aspects of the European territory, which are either interpreted as “thresholds” to be overcome in the name of a model of United Europe – “integral totality” – or are instead regarded as insurmountable obstacles for a Europe that is irreparably and perhaps, according to anti-Europeanists, fortunately fragmented – “partitive totality”. Further, this is to be done without excluding the possibility of contradictory and complementary solutions to these binary visions. In this context the book analyzes various texts in order to obtain a more precise picture of the clash, reveal its semiotic forms, and by doing so, identify a way out of the crisis.
Images of Organization: 30th Anniversary Edition
by Professor Gareth MorganSince its first publication over twenty years ago, Images of Organization has become a classic in the canon of management literature. The book is based on a very simple premise—that all theories of organization and management are based on implicit images or metaphors that stretch our imagination in a way that can create powerful insights, but at the risk of distortion. Gareth Morgan provides a rich and comprehensive resource for exploring the complexity of modern organizations internationally, translating leading-edge theory into leading-edge practice.
Images of Organization: 30th Anniversary Edition
by Professor Gareth MorganSince its first publication over twenty years ago, Images of Organization has become a classic in the canon of management literature. The book is based on a very simple premise—that all theories of organization and management are based on implicit images or metaphors that stretch our imagination in a way that can create powerful insights, but at the risk of distortion. Gareth Morgan provides a rich and comprehensive resource for exploring the complexity of modern organizations internationally, translating leading-edge theory into leading-edge practice.
Images of a Constitution (Routledge Revivals)
by William E. ConklinOriginally published in 1989, in this remarkable conjunction of constitutional theory, jurisprudence, literary theory, constitutional law, and political theory, William Conklin first tells us what a constitution is not: it is not a text, nor a compendium of judicial and legislative decisions interpreting a text, nor a set of doctrines, nor moral/political values, nor customs, nor a priori conceptions. A constitution, he argues, is an image which exists through the legal consciousness of a community.Using a wide range of Canadian judicial decisions as examples, Conklin shows that the classic cases have been those where the boundaries of two conflicting images clashed. In each instance, the subject-matter itself collapses into a search for a coherent image of what a constitution is all about.The dominant image of a constitution in Canadian judicial discourse has been a rationalist one emanating from the Enlightenment understanding of knowledge. Turning to academic writings on Canadian federalism law, Conklin goes on to identify clearly the boundaries of three versions of rationalism, and to show that Canadian scholars have shared with judges the dominant image of rationalism.In the third part of his essay, the author makes a prescriptive claim, namely that a text such as the Canadian Charter of Rights and Freedoms arguably raises issues which the rationalist image of a constitution precludes as legitimate inquiries. He identifies a further general image of a constitution in Canadian legal discourse, a teleological one which is rooted in the writings and judgments of Ivan Rand. Finally, he uses the contours of the Rand image to work out a further image of constitution, an image that allows lawyers to entertain issues of both theory and social/cultural practice, thereby placing them in a position to alleviate the pain and suffering of those in need.
Images of the Present Time (The Seminars of Alain Badiou)
by Alain BadiouAlain Badiou began the twenty-first century by considering the relationship between philosophy and notions of “the present.” In this period of his ongoing annual lecture series, the acclaimed philosopher took up the existential problem of how to be contemporary with one’s own time—that is, how to not simply inhabit a passing moment but bring a real present into existence.Images of the Present Time presents nearly three years of Badiou’s seminars, held from 2001 to 2004, partly against the backdrop of the war in Iraq. Given while Badiou was writing Logics of Worlds, the second of the three volumes of Being and Event, these lectures address some of the same questions of existence in a particular world in a more personal and conversational tone, with reference to literature, philosophy, and contemporary politics and culture. He proposes a new concept of living in a real present as the twisting together of something from the past and something of the future.Featuring some of the philosopher’s most inspiring and approachable work, Images of the Present Time is an important book for all readers interested in the practical as well as conceptual possibilities of Badiou’s thought.
Imaging Atlas of the Normal Gallbladder and Its Variants
by J.W. MeilstrupAn in-depth knowledge of the wide spectrum of normal gallbladder appearances is vital to appropriate clinical workup and the correct diagnosis of patients with upper abdominal symptoms. This book covers the range of appearances of the normal gallbladder and its variants, including discussions of anatomy, embryology, and imaging techniques to promote a better understanding of the subject. Anomalies of number, location, and form are each addressed in separate chapters, and discussions of imaging artifacts of the gallbladder and pseudolesions, which can mimic gallbladder disease, are also included. A short chapter on the appearance of the fetal gallbladder is included to round out this comprehensive volume.
Imaging and Imagining the Fetus: The Development of Obstetric Ultrasound
by Malcolm Nicolson John E. FlemingHow engineers and clinicians developed the ultrasound diagnostic scanner and how its use in obstetrics became controversial.To its proponents, the ultrasound scanner is a safe, reliable, and indispensable aid to diagnosis. Its detractors, on the other hand, argue that its development and use are driven by the technological enthusiasms of doctors and engineers (and the commercial interests of manufacturers) and not by concern to improve the clinical care of women. In some U.S. states, an ultrasound scan is now required by legislation before a woman can obtain an abortion, adding a new dimension to an already controversial practice. Imaging and Imagining the Fetus engages both the development of a modern medical technology and the concerted critique of that technology.Malcolm Nicolson and John Fleming relate the technical and social history of ultrasound imaging—from early experiments in Glasgow in 1956 through wide deployment in the British hospital system by 1975 to its ubiquitous use in maternity clinics throughout the developed world by the end of the twentieth century. Obstetrician Ian Donald and engineer Tom Brown created ultrasound technology in Glasgow, where their prototypes were based on the industrial flaw detector, an instrument readily available to them in the shipbuilding city. As a physician, Donald supported the use of ultrasound for clinical purposes, and as a devout High Anglican he imbued the images with moral significance. He opposed abortion—decisions about which were increasingly guided by the ultrasound technology he pioneered—and he occasionally used ultrasound images to convince pregnant women not to abort the fetuses they could now see.Imaging and Imagining the Fetus explores why earlier innovators failed where Donald and Brown succeeded. It also shows how ultrasound developed into a "black box" technology whose users can fully appreciate the images they produce but do not, and have no need to, understand the technology, any more than do users of computers. These "images of the fetus may be produced by machines," the authors write, "but they live vividly in the human imagination."
Imagining Justice
by John P. CrankImagining Justice seeks to move away from normative thinking about justice, particularly in the area of justice education, suggesting that what is needed today is a way to think about the enterprise of justice that will capture its full potential. By providing an introduction to the intellectual potential of the field of justice, we can acknowledge that the field is wider than formerly recognized, and ultimately imagine the full richness that justice can encompass.
Imagining New Legalities: Privacy and Its Possibilities in the 21st Century
by Austin Sarat Lawrence Douglas Martha UmphreyImagining New Legalitiesreminds us that examining the right to privacy and the public/private distinction is an important way of mapping the forms and limits of power that can legitimately be exercised by collective bodies over individuals and by governments over their citizens. This book does not seek to provide a comprehensive overview of threats to privacy and rejoinders to them. Instead it considers several different conceptions of privacy and provides examples of legal inventiveness in confronting some contemporary challenges to the public/private distinction. It provides a context for that consideration by surveying the meanings of privacy in three domains--the first, involving intimacy and intimate relations; the second, implicating criminal procedure, in particular, the 4th amendment; and the third, addressing control of information in the digital age. The first two provide examples of what are taken to be classic breaches of the public/private distinction, namely instances when government intrudes in an area claimed to be private. The third has to do with voluntary circulation of information and the question of who gets to control what happens to and with that information.
Imagining World Order: Literature and International Law in Early Modern Europe, 1500–1800
by Chenxi TangIn early modern Europe, international law emerged as a means of governing relations between rapidly consolidating sovereign states, purporting to establish a normative order for the perilous international world. However, it was intrinsically fragile and uncertain, for sovereign states had no acknowledged common authority that would create, change, apply, and enforce legal norms. In Imagining World Order, Chenxi Tang shows that international world order was as much a literary as a legal matter. To begin with, the poetic imagination contributed to the making of international law. As the discourse of international law coalesced, literary works from romances and tragedies to novels responded to its unfulfilled ambitions and inexorable failures, occasionally affirming it, often contesting it, always uncovering its problems and rehearsing imaginary solutions.Tang highlights the various modes in which literary texts—some highly canonical (Camões, Shakespeare, Corneille, Lohenstein, and Defoe, among many others), some largely forgotten yet worth rediscovering—engaged with legal thinking in the period from the sixteenth to the eighteenth century. In tracing such engagements, he offers a dual history of international law and European literature. As legal history, the book approaches the development of international law in this period—its so-called classical age—in terms of literary imagination. As literary history, Tang recounts how literature confronted the question of international world order and how, in the process, a set of literary forms common to major European languages (epic, tragedy, romance, novel) evolved.
Imagining a Way: Exploring Reformed Practical Theology And Ethics
by Clive PearsonFrom the inception of the Reformed tradition, Reformed Christians have followed God's call to engage and change the world. Yet little work has been done to bring the tools of practical theology and ethics to bear on the task of understanding the Reformed tradition. This comprehensive volume addresses that problem. It gathers some of the most respected voices from within the study of Christian ethics and practical theology to ask how the Reformed tradition understands its calling into the world. What does being Reformed mean for how one engages the ills of racism, white supremacy, and homophobia? What does it mean for an environmental ethic? How does Reformed preaching and liturgy respond to sexual violence? These are among the many important issues this book seeks to address. Readers will come away with a firmer grasp of how the Reformed tradition informs and animates Christian engagement with the world. <P><P>Contributors include Denise Ackermann, Jana Childers, Susan Davies, Etienne de Villiers, Cynthia Jarvis, Jong Hyuk Kim, Ralph Kunz, Cam Murchison, Piet Naudé, Cornelius Plantinga, Nancy Ramsay, Kang Phee Ramsay, Dirk Seng, Max Smit Stackhouse, William Storrar, Geoff Thompson, and Hmar Vanlalauva.
Imagining the International: Crime, Justice, and the Promise of Community (The Cultural Lives of Law)
by Nesam McMillanInternational crime and justice are powerful ideas, associated with a vivid imagery of heinous atrocities, injured humanity, and an international community seized by the need to act. Through an analysis of archival and contemporary data, Imagining the International provides a detailed picture of how ideas of international crime (crimes against all of humanity) and global justice are given content, foregrounding their ethical limits and potentials. Nesam McMillan argues that dominant approaches to these ideas problematically disconnect them from the lived and the specific and foster distance between those who have experienced international crime and those who have not. McMillan draws on interdisciplinary work spanning law, criminology, humanitarianism, socio-legal studies, cultural studies, and human geography to show how understandings of international crime and justice hierarchize, spectacularize, and appropriate the suffering of others and promote an ideal of justice fundamentally disconnected from life as it is lived. McMillan critiques the mode of global interconnection they offer, one which bears resemblance to past colonial global approaches and which seeks to foster community through the image of crime and the practice of punitive justice. This book powerfully underscores the importance of the ideas of international crime and justice and their significant limits, cautioning against their continued valorization.
Imbeciles: The Supreme Court, American Eugenics, and the Sterilization of Carrie Buck
by Adam CohenLonglisted for the 2016 National Book Award for NonfictionOne of America’s great miscarriages of justice, the Supreme Court’s infamous 1927 Buck v. Bell ruling made government sterilization of “undesirable” citizens the law of the land In 1927, the Supreme Court handed down a ruling so disturbing, ignorant, and cruel that it stands as one of the great injustices in American history. In Imbeciles, bestselling author Adam Cohen exposes the court’s decision to allow the sterilization of a young woman it wrongly thought to be “feebleminded” and to champion the mass eugenic sterilization of undesirable citizens for the greater good of the country. The 8–1 ruling was signed by some of the most revered figures in American law—including Chief Justice William Howard Taft, a former U.S. president; and Louis Brandeis, a progressive icon. Oliver Wendell Holmes, considered by many the greatest Supreme Court justice in history, wrote the majority opinion, including the court’s famous declaration “Three generations of imbeciles are enough.”Imbeciles is the shocking story of Buck v. Bell, a legal case that challenges our faith in American justice. A gripping courtroom drama, it pits a helpless young woman against powerful scientists, lawyers, and judges who believed that eugenic measures were necessary to save the nation from being “swamped with incompetence.” At the center was Carrie Buck, who was born into a poor family in Charlottesville, Virginia, and taken in by a foster family, until she became pregnant out of wedlock. She was then declared “feebleminded” and shipped off to the Colony for Epileptics and Feeble-Minded.Buck v. Bell unfolded against the backdrop of a nation in the thrall of eugenics, which many Americans thought would uplift the human race. Congress embraced this fervor, enacting the first laws designed to prevent immigration by Italians, Jews, and other groups charged with being genetically inferior. Cohen shows how Buck arrived at the colony at just the wrong time, when influential scientists and politicians were looking for a “test case” to determine whether Virginia’s new eugenic sterilization law could withstand a legal challenge. A cabal of powerful men lined up against her, and no one stood up for her—not even her lawyer, who, it is now clear, was in collusion with the men who wanted her sterilized.In the end, Buck’s case was heard by the Supreme Court, the institution established by the founders to ensure that justice would prevail. The court could have seen through the false claim that Buck was a threat to the gene pool, or it could have found that forced sterilization was a violation of her rights. Instead, Holmes, a scion of several prominent Boston Brahmin families, who was raised to believe in the superiority of his own bloodlines, wrote a vicious, haunting decision upholding Buck’s sterilization and imploring the nation to sterilize many more. Holmes got his wish, and before the madness ended some sixty to seventy thousand Americans were sterilized. Cohen overturns cherished myths and demolishes lauded figures in relentless pursuit of the truth. With the intellectual force of a legal brief and the passion of a front-page exposé, Imbeciles is an ardent indictment of our champions of justice and our optimistic faith in progress, as well as a triumph of American legal and social history.From the Hardcover edition.
Imitación y experiencia (Tetralogía de la Ejemplaridad)
by Javier Gomá LanzónImitación y experiencia establece los fundamentos de una teoría general de la ejemplaridad, con su parte pragmática y su parte metafísica, poniendo así los cimientos filosóficos sobre los que descansan los otros tres títulos de esta tetralogía. La imitación es una de esas ideas fundamentales de la cultura occidental que, como la del ser, recorre todo el pensamiento europeo de un extremo a otro. <P><P>Para crear el contexto de comprensión adecuado, este libro, como paso previo, recupera una tradición de conceptos clásicos de la cultura como los de modelo, ejemplo o imitación. A través de una extensa investigación, reúne y ordena el vasto material bibliográfico disponible para narrar por primera vez la historia de la teoría de la ejemplaridad desde los orígenes hasta nuestros días distinguiendo entre cuatro clases de imitación y tres grandes etapas culturales. <P><P> Cada uno de los títulos de esta tetralogía es autónomo y de lectura independiente y al mismo tiempo los cuatro forman parte de un plan unitario en torno a la idea de ejemplaridad: su historia y su teoría general (Imitación y experiencia), su formación subjetiva (Aquiles en el gineceo), su aplicación a la esfera política (Ejemplaridad pública) y su relación con la esperanza (Necesario pero imposible). Esta edición culmina un plan literario-filosófico muy antiguo y largamente cultivado por el autor.
Imitation in Early Christianity: Mimesis and Religious-Ethical Formation
by Cornelis BennemaWhat did exhortations to &“follow Jesus&” or &“imitate Christ&” mean to early Christians? Cornelis Bennema examines mimesis as a religious-ethical concept in early Christianity—the imitation of Jesus (and other exemplars) to become a better, more Christlike person. Situating appeals for imitation in the New Testament and Apostolic Fathers within the cultural and social context of the broader Greco-Roman world, Bennema shows how early Christian mimesis was not about literal replication, but instead was a creative, cognitive, and transformative means for shaping conduct and character. As part of this study, Bennema explores key questions about the historic origins of early Christian mimesis; the language that early Christian authors used to articulate the concept of mimesis; the scope, nature, and workings of mimesis in each major section of early Christian literature; and how early Christians navigated the challenges of imitating exemplars (such as Paul or Jesus) who were not physically present. Offering well-researched answers to these questions, Bennema provides readers with a nuanced and informative picture of exhortations to imitation in the New Testament and Apostolic Fathers.
Immanuel Kant's Groundwork for the Metaphysics of Morals: A Commentary
by Immanuel Kant Allen W. Wood Dieter SchöneckerA defining work of moral philosophy, Kant's Groundwork for the Metaphysics of Morals has been influential to an extent far beyond what its modest length (roughly 75 pages) might suggest. It is also a famously difficult work, concerned with propounding universal principles rather than answering practical questions. As even professional philosophers will admit, first-time readers are not alone in finding some of its arguments perplexing. Offering an introduction that is accessible to students and relevant to specialized scholars, Dieter Schönecker and Allen Wood make luminously clear the ways the Groundwork for the Metaphysics of Morals forms the basis of our modern moral outlook: that all human beings have equal dignity as ends in themselves; that every rational being is a self-governing agent whose morality freely derives from his or her own will; and that all rational beings constitute an ideal community, bound only by the moral laws they have agreed upon. Schönecker and Wood explain key Kantian concepts of duty, the good will, and moral worth, as well as the propositions Kant uses to derive his conception of the moral law. How the law relates to freedom, and the significance of the free will within Kant's overall philosophy are rigorously interrogated. Where differing interpretations of Kant's claims are possible, the authors provide alternative options, giving arguments for each. This critical introduction will help readers of the Groundwork gain an informed understanding of Kant's challenging but central philosophical work.
Immanuel Kant: Groundwork of the Metaphysics of Morals in Focus (Routledge Philosophers In Focus Ser.)
by Lawrence PasternackThe Groundwork of the Metaphysics of Morals^ is one of the most important works of moral philosophy ever written, and Kant's most widely read work. It attempts to demonstrate that morality has its foundation in reason and that our wills are free from both natural necessity and the power of desire. It is here that Kant sets out his famous and controversial 'categorical imperative', which forms the basis of his moral theory.This book is an essential guide to the groundwork and the many important and profound claims that Kant raises. The book combines an invaluable introduction to the work offering an exploration of these arguments and setting them in the context of Kant's thinking, along with the complete H.J Paton translation of the work, and a selection of six of the best contemporary commentaries. It is the ideal companion for all students of Kantian ethics and anyone interested in moral philosophy. _ _ _
Immersive Technology and Experiences: Implications for Business and Society
by Githa S. Heggde Santosh Kumar Patra Rasananda PandaThis book provides a comprehensive overview of the role of immersive technology with multiple sectoral perspectives, such as entertainment, education, health care, and more. It covers a detailed analysis of the latest trends and developments in the field. It encompasses practical insights on using immersive technology effectively through industry expert chapters, case studies, and real-world examples that demonstrate how immersive technology is being used in different industries. Chapters in this book are from academicians and industry professionals to create a fine balance of knowledge and practice perspective of today’s immersive technology. It is written in accessible language that is easy for non-experts to understand. It focuses on the future of immersive technology, exploring its potential impact on society and the economy. It provides insights into the challenges and opportunities that lie ahead and offers predictions on how immersive technology will continue to evolve in the years to come. It is a valuable resource for anyone learning more about immersive technology.
Immigrant America: A Portrait
by Prof. Alejandro Portes Prof. Rubén G. RumbautThis revised and updated fifth edition of Immigrant America: A Portrait provides a comprehensive and current overview of immigration to the United States, including its history, the principal theories seeking to account for its diverse origins, the main types of immigrants, and the various forms of immigrants' incorporation within American society. With the latest available data, Immigrant America further explores the economic, political, regional, linguistic, and religious aspects of immigration. It offers detailed analyses of the adaptation process experienced by adult children of immigrants and adds an updated and expanded concluding chapter on changing immigration policy regimes both past and present.